Edge Point Group Releases Executive Guide to Digital Exposure: Revealing How Public Clues Quietly Create Risk
Why what you share (and what’s shared about you) still matters—and how to live just a little quieter, starting today.
The release comes as public concern grows around impersonation scams, targeted violence, and AI-driven profiling. These threats increasingly rely not on hacking but on open-source intelligence, where threat actors build comprehensive narratives from publicly available data trails.
“Digital exposure isn’t just about what someone posts,” said a spokesperson for Edge Point Group. “It’s the accumulation of everything others can access—what’s archived, cached, copied, or sold. These aren’t isolated details. They form patterns.”
________________________________________
1. Understanding Digital Exposure: More Than Just What You Share
Edge Point Group defines digital exposure as the complete surface area someone presents, whether intentionally or not. It includes:
• Posts from friends, family, or third parties
• Public records, filings, and news articles
• Metadata in photos or documents
• Mentions in forums, speaker bios, or alumni networks
• Information purchased and resold by data brokers
Even individuals who post infrequently often leave behind years of material that can be scraped, cross-referenced, and monetized—or misused.
For example, a business owner who registered an LLC in their home state might have exposed their residential address. Combined with public donations, travel photos, or a child’s school content online, that data creates a comprehensive footprint that can be used for targeted advertising.
________________________________________
2. Who Faces the Greatest Risk?
While every digital footprint carries some level of exposure, the consequences vary depending on the context. The guide breaks down standard profiles:
• Executives & Founders: SEC filings, industry interviews, keynote appearances, and personal domains make it easy to build timelines and relationship maps.
• High-Net-Worth Individuals: Real estate disclosures, yacht registries, social media content, and luxury branding attract profiling, especially when lifestyle cues intersect with publicly available family data.
• Professionals and public figures: Resumes, LinkedIn comments, podcast appearances, and board memberships all contribute to establishing traceable routines.
• Families & Teenagers: Posts from children or extended family, especially around travel, school events, or milestone moments, often reveal more than intended.
“Exposure becomes dangerous when patterns become predictable,” the guide explains.
________________________________________
3. Where Exposure Hides in Plain Sight
The guide lists six high-risk categories where exposure often goes unnoticed:
• Search Engines: Outdated results, PDFs, cached versions of deleted content
• Data Brokers: Whitepages, Spokeo, BeenVerified, and hundreds more
• Images: EXIF data, reflections in sunglasses, license plates, background books, or house layouts
• Social Platforms: Tagged photos, public comments, group memberships, timestamps, and location check-ins
• Domains & LLCs: WHOIS data, trademark filings, state business registries
• Public Mentions: Event programs, press releases, review sites, organizational newsletters
Each item may seem low-risk individually, but in aggregate, they form patterns that are easy to exploit.
________________________________________
4. Why Exposure Grows—Even Without New Posts
Many assume that deleting a few old accounts or “going quiet” online reduces their exposure. However, digital trails don’t fade unless they are deliberately removed.
Examples include:
• Google still indexes dormant social media profiles
• Public fundraising pages revealing family ties and locations
• Forum accounts created decades ago are still active in background databases
• Cached articles listing home cities or political affiliations
• Photos posted by others showing private property or security vulnerabilities
Even well-meaning posts—such as congratulating someone on a promotion or retirement—can reveal timelines and career moves that adversaries can study.
________________________________________
5. The Habits That Quietly Amplify Risk
Edge Point Group highlights several behaviors that seem harmless but increase exposure exponentially:
• Reusing email addresses or usernames across personal and professional platforms
• Allowing assistants or contractors to manage social media without strict guidance
• Auto-filling forms on unfamiliar websites
• Commenting on public-facing articles or LinkedIn, especially around controversial topics
• Using one phone number across financial, telecom, and social ecosystems
A typical example is someone filling out a luxury sweepstakes or real estate inquiry form using their email address. That address may now be sold, repackaged, and linked to demographic markers, making it easier for scammers or opportunists to profile.
________________________________________
6. Reducing Exposure Without Going Off-Grid
Rather than fear-based advice, the guide offers a structured, repeatable process:
A. Audit
• Run searches using name + city, email, or company
• Review public profiles, bios, and any press
• Use breach-monitoring tools like HaveIBeenPwned
B. Clean
• Remove or update outdated bios, resumes, or domain listings
• Submit opt-out requests to major data brokers
• Lockdown or anonymize personal websites
C. Adapt
• Delay posts by 24–72 hours
• Avoid tagging locations while in transit
• Use business-only contact channels for inbound requests
D. Monitor & Educate
• Set quarterly reminders for visibility reviews
• Use browser extensions and private search engines
• Train family and staff on basic exposure hygiene
“This isn’t about vanishing,” the firm emphasizes. “It’s about thinking like a threat actor—and closing the loops before someone else finds them.”
________________________________________
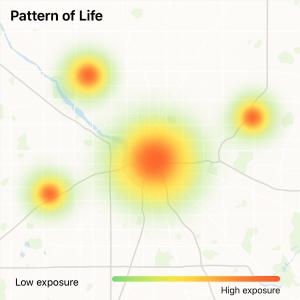
7. Why This Matters Now
The guide concludes with a sobering warning: AI has significantly accelerated the speed and scale of pattern recognition. In the past, building a personal profile used to take hours. Now, it takes seconds.
Recent incidents—from doxxing campaigns to targeted attacks on public figures—often started with open-source exposure, not cyber intrusion. And most involved:
• Visible address or travel habits
• Predictable routines or posting schedules
• Missed warning signs in how people’s digital lives intersect with
“Increased visibility used to mean influence,” said the spokesperson. “Now, it also means exposure.”
________________________________________
About Edge Point Group
Edge Point Group is a private intelligence and security consultancy specializing in exposure reduction, digital footprint assessments, and personal risk mapping. The firm serves executives, founders, and family offices,
Ian Haisler
Edge Point Group LLC
+1 949-939-2814
email us here
Visit us on social media:
LinkedIn
Instagram
X
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.
Audfly Technology Unveils New Alpha Series Modules, Advancing the Future of Directional Sound
Miami Dade Apostille Expands Access to Fast, Secure International Document Certification
PlanckMan - The Retro Game That Never Was Officially Launches on Steam, YouTuber Creates Custom Arcade Machine
Więcej ważnych informacji
 Jedynka Newserii
Jedynka Newserii

 Jedynka Newserii
Jedynka Newserii
Konsument

Grupa nowych biednych emerytów stale się powiększa. Ich świadczenie jest znacznie poniżej minimalnej emerytury
Przybywa osób, które z powodu zbyt krótkiego czasu opłacania składek pobierają emeryturę niższą od minimalnej. Tak zwanych nowych biednych emerytów jest w Polsce ok. 430 tys., a zdecydowaną większość grupy stanowią kobiety – wskazują badania ekspertów Instytutu Pracy i Spraw Socjalnych. W ich przypadku krótszy okres składkowy zwykle wynika z konieczności opieki nad dziećmi lub innymi osobami w rodzinie. Wśród innych powodów, wymienianych zarówno przez panie, jak i panów, są także praca za granicą lub na czarno oraz zły stan zdrowia.
Media i PR
M. Wawrykiewicz (PO): Postępowanie z art. 7 przeciw Węgrom pokazało iluzoryczność tej sankcji. Unia wywiera naciski poprzez negocjacje nowego budżetu

Przykład Węgier pokazał, że procedura z artykułu 7 traktatu o UE o łamanie praworządności nie ma mocy prawnej z powodu braku większości, nie mówiąc o jednomyślności wśród pozostałych państw członkowskich. Negocjacje nowego budżetu UE to dobry pretekst do zmiany sposobu części finansowania z pominięciem rządu centralnego. Czerwcowy marsz Pride w Budapeszcie pokazał, że część społeczeństwa, głównie stolica, jest przeciwna rządom Viktora Orbána, ale i na prowincji świadomość konsekwencji działań Fideszu staje się coraz większa przed przyszłorocznymi wyborami.
Firma
Blockchain zmienia rynek pracy i edukacji. Poszukiwane są osoby posiadające wiedzę z różnych dziedzin

Zapotrzebowanie na specjalistów od technologii blockchain dynamicznie rośnie – nie tylko w obszarze IT, ale również w administracji, finansach czy logistyce. Coraz więcej uczelni wprowadza programy związane z rozproszonymi rejestrami, które wyposażają studentów w umiejętności odpowiadające wymogom rynku.
Partner serwisu
Szkolenia

Akademia Newserii
Akademia Newserii to projekt, w ramach którego najlepsi polscy dziennikarze biznesowi, giełdowi oraz lifestylowi, a także szkoleniowcy z wieloletnim doświadczeniem dzielą się swoją wiedzą nt. pracy z mediami.



![Nestlé w Polsce podsumowuje wpływ na krajową gospodarkę. Firma wygenerowała 0,6 proc. polskiego PKB [DEPESZA]](https://www.newseria.pl/files/1097841585/fabryka-nesquik_1,w_85,r_png,_small.png)






.gif)

 |
| |
| |
|